output devices
arduino sketch (breadboard pins)
arduino sketch (milled board pins)
mcu som: rp2040 xiao
Reader Module: HiLetgo RFID Kit
Test Cards: LEXI UID PVC Blanks
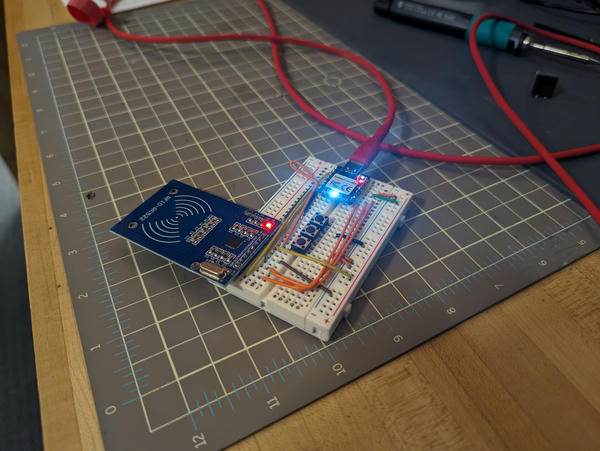
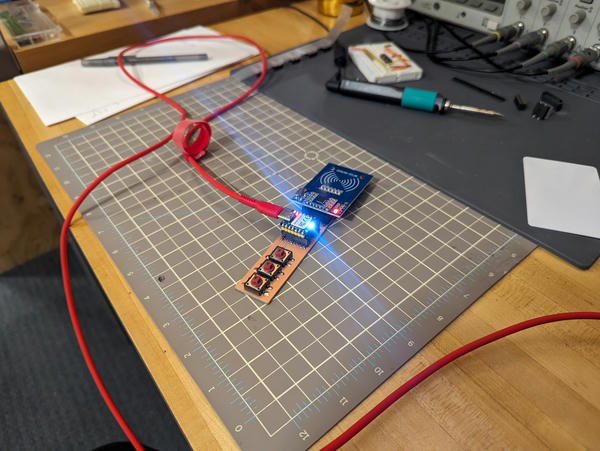
This week, I upgraded the reader I made last week. It now supports cloning the UID of a Mifare Classic 1K card to a new card, wiping the card, and unlocking certain cards for writing. The cloner mode can be changed with the buttons, and the current mode is displayed on the colored LED, as well as over serial.
This is an output device in the sense that we're using the reader in a write mode, or from a human interface perspective in the sense that the LED indicates the mode.
Colors:
- light blue: reader, no key or default key loaded
- dark blue: reader, non-default key loaded
- yellow: unlock mode
- pink: writer mode
- orange: write default key
Button input scheme (1 to 3, top to bottom respectively):
- 1: read mode
- 2: unlock mode
- 3: write mode (fails if no key has been read)
- 1 + 2: clear stored key
- 2 + 3: write default key
Milled board (read):
Milled board (write):
Milled board (unlock):
Going through all the operations on the breadboard version:
serial output / event trace
read card (sak: 0x08), uid: 0925263e
[int] mode: write
overwriting card: 0925263e
wrote card
new serial: 0925263e
[int] mode: unbrick
unbricked uid sector
[int] mode: write
[int] entered write-zero mode
[int] mode: write
overwriting card: 01020304
wrote card
new serial: a5a5a5a5
[int] mode: write
[int] erased key
[int] mode: read
summary
-
Read a card, storing the UID.
-
a. Press the write button, entering write mode
b. Present the same card, reading the serial
c. Overwrite it with the same serial (no-op, for demo)
-
a. Enter unbrick (unlock) mode
b. Present card, unbrick ok (no-op)
-
a. Press write and unbrick buttons (write-zero mode)
b. Present card, overwrite UID with a5a5a5a5 (dummy sequence)
-
Press read button, returning to read mode
[int] lines are interrupt-triggered button presses.
security notes
In general, for secured card systems (those which store and use cryptographic material onboard the cards), a capability which Mifare Classic 1K supports, producing a card with a duplicate UID does not pose a security risk. Cards with cloned UIDs have no capacity to authenticate the user without the key material.
That said, Mifare Classic 1K has been cracked -- it is possible to exfiltrate key material and fully clone a card -- but this process takes time, as the card must be attacked repeatedly, and my system does not attempt to do this.
If, however, an institution were to be so obtuse as to only use the world-readable and trivially-writable UID as the sole source of authentication information, it would be possible to use this device to functionally replicate user cards freely and, for instance, share card access between potentially-unauthorized principals.
I don't know of an institution like that, though.
board design notes
I used 2x8 0.1"-pitch SMD header sockets to accept both the card reader and the MCU, in order to allow me to reuse them between board revisions, if required.