Ben Z. Yuan - How to Make Almost Anything
Project: A Hardware Password Manager
Project
For my final project I built a hardware password manager.

Why
Existing software password managers, like LastPass, 1Password, KeePass, …, are very good at managing all of our network service passwords, so we can have different passwords for Facebook, Twitter, LinkedIn, Google, Steam, and other such websites. However, they suffer from one common problem: you have to be logged in to some computer to access them. This means that you can’t (effectively) use them to manage your terminal login passwords, since you aren’t logged in when you need to type them!
At MIT, you use your Athena credentials to log in to many internal websites, but you also use your Athena password to log yourself in to any one of the various physical terminals on campus. If you don’t have a computer of your own, it becomes harder to use a strong unique password for your Athena account like you’re supposed to, because you can’t rely on KeePass etc. to remember it for you.
You could create some application on a smartphone to keep your passwords. But then you run into some problems:
- You have to trust that your smartphone and its operating system aren’t surreptitiously sending your passwords somewhere else.
- You still have to transcribe and type your password in by hand - meaning that someone looking over your shoulder can learn it!
- You now have to secure your phone against people who want to “borrow” it.
We solve these issues by creating a dedicated hardware device that anyone with access to fabrication tools should be able to assemble.
Prior art
This is not the first hardware password manager by any means; you can buy or build devices right now that mostly do the same thing.
Mooltipass ($80)
Things we like
- Emulates a USB keyboard
- Encrypts credentials on-device (with separate smart card)
- Open hardware and firmware
- Tiny!
- Extremely tamper-evident
Things we don’t like
- Requires separate software to preload or generate credentials
Pastilda ($50)
Things we like
- Emulates a USB keyboard
- Open hardware and firmware
- Encrypts credentials on-device in KeePass-compatible format
- Tiny!
Things we don’t like
- Requires preloading of device credentials
FinalKey ($??)
Things we like
- Emulates a USB keyboard
- Open hardware and firmware
- Encrypts credentials on-device
- Generates credentials on-device
Things we don’t like
- Requires separate companion software to operate
What was designed
- a (formidable) mainboard constructed around a AT90USB1286
- with 20-pin header for a OLED display breakout board
- with 6-pin header to connect to an I2C-based peripheral
- with an integrated copy of the OneRNG circuit
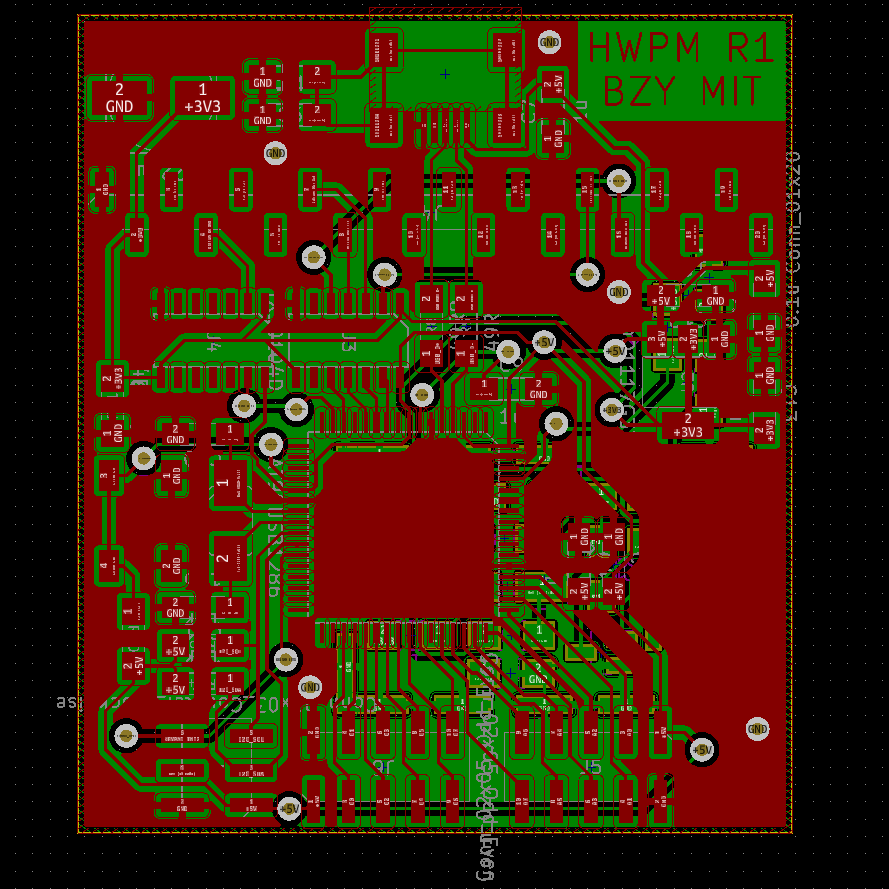
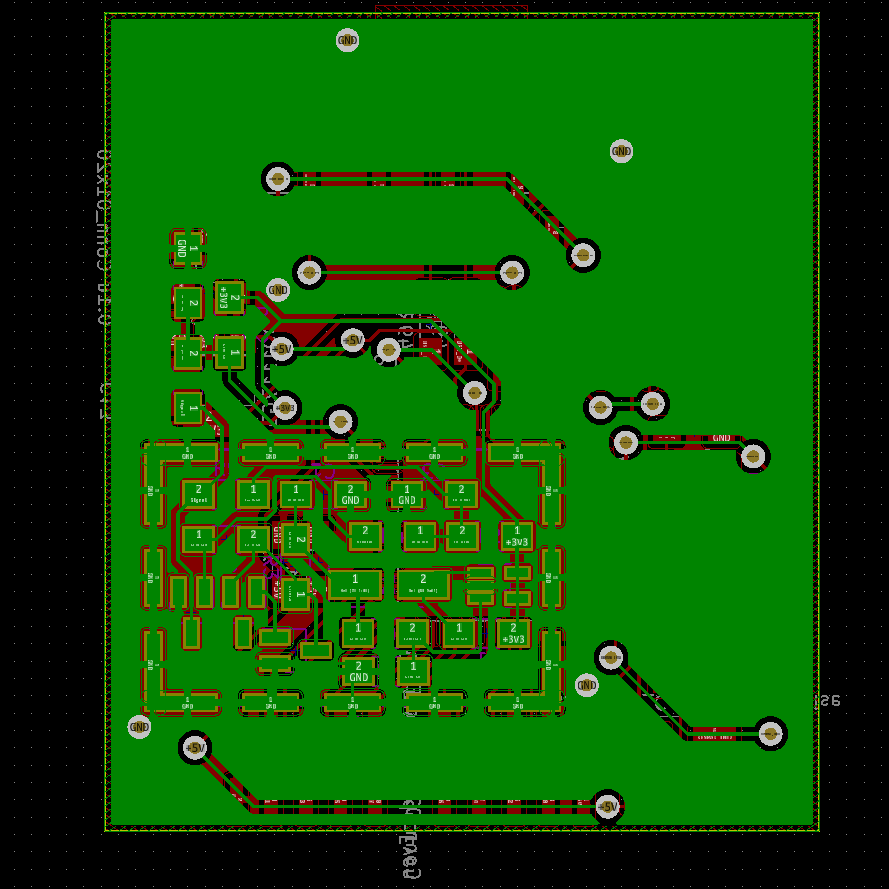
-
a 3D-printable (or millable from rigid stock) two-part enclosure
- with internal trays for the mainboard and input device
- with holes for the input device buttons
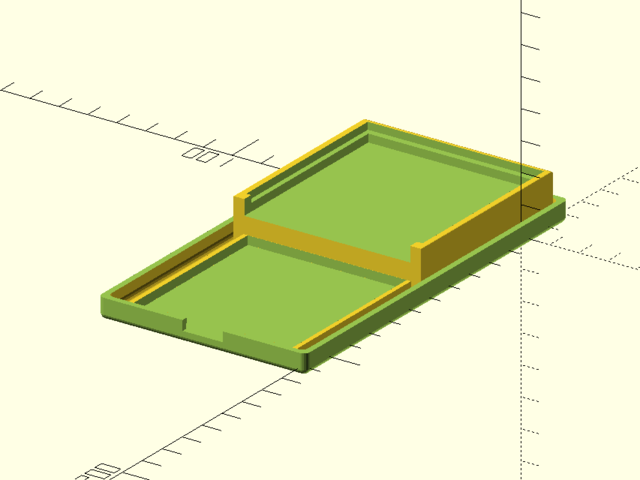
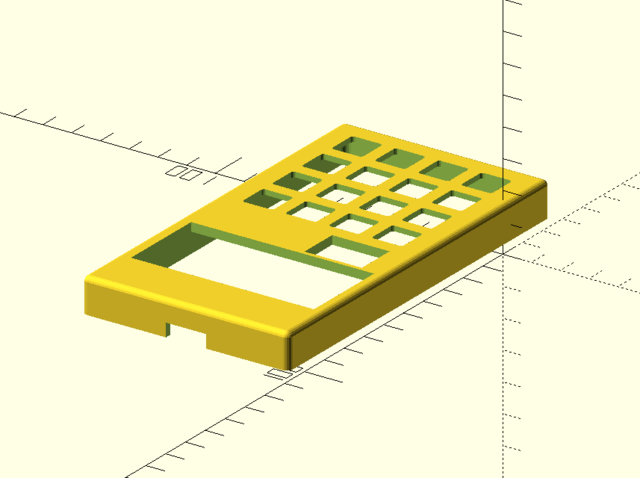
- STL files
- caution: needs extra 3-4mm “spacer” material
Parts manifest
- 1x double-sided FR-1 circuit board stock ($1.28, Bantam Tools)
- 1x AT90USB1286-AURCT-ND ($8.32, DigiKey)
- 1x H2961CT-ND USB-mini connector ($0.99, DigiKey, on inventory)
- 1x Abracon ABM3-16.000MHZ-D2Y-T ($0.69, DigiKey)
- 2x TXS0104EDR bidirectional level shifters ($1.38 x2, DigiKey)
- 1x ZLDO1117G33TA 3.3V regulator ($0.50, DigiKey, on inventory)
- 1x 20-pin 0.1” SMD female header (on inventory as 2x 10-pin headers, $1.23 individual x2)
- 1x 2x3 0.1” SMD male header ($0.60 from lot of 100, on inventory)
- 1x AP3015 boost converter ($0.73, DigiKey)
- 1x 10uH 1206 SMD inductor 535-11657-1-ND ($0.35, DigiKey)
- 1x 1206 SMD ferrite 732-1623-1-ND ($0.24, DigiKey)
- 3x MMBT3904 NPN SMD transistors ($0.19 x 3, DigiKey)
- assorted 1206 SMD resistors ($0.00637 each from lots of 1000, except where noted):
- 2x 49R9
- 1x 1M
- 3x 10K
- 1x 49K9
- 1x 4K99
- 1x 1K
- 1x 499
- 2x 470K 1% ($0.0136 x 2 from lot of 100, DigiKey)
- 1x 27K 1% ($0.0213 from lot of 100, DigiKey)
- 2x 4K7 1% ($0.0136 x 2 from lot of 100, DigiKey)
- assorted 1206 SMD capacitors (from lots of 500 except where noted):
- 1x 10000p ($0.04)
- 3x 1u ($0.07 x 3)
- 2x 10p ($0.04 x 2)
- 5x 0.1u ($0.12 x 5)
- 1x 10u ($0.18, from lot of 100)
- 1x 220u electrolytic 493-2098-1-ND (8mm radial, $0.33 individual, DigiKey)
- 1x Adafruit Trellis PCB ($9.95, Adafruit)
- 1x Adafruit Trellis silicone elastomer keypad ($4.95, Adafruit)
- 1x Adafruit 128x32 2.3” blue OLED ($39.95, Adafruit)
Total: $74.65
What was built
- two iterations of a project board


- some nice system software
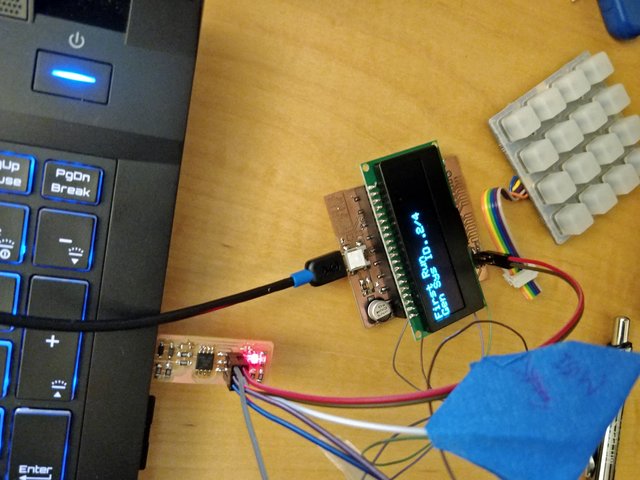
- a hardware password manager!
- that lets you specify an unlock passcode at first run
- that stores, types back, and allows on-board (re)generation of up to 4 passwords
- that protects its passwords at rest with strong(…ish) cryptography
- 256-bit master key derived from 32-bit unlock code and random 256-bit per-device salt with 25-round PBKDF2-SHA3
- passwords encrypted with ChaCha20-Poly1305
- that can be reset

Processes used
- lots of milling and hand soldering (for PCB)
- 3D printing (for enclosure)
Evaluation
- It does the thing we wanted it to do.
- People seemed to be impressed during the open house.
- Speculatively you could (though we didn’t):
- conduct a security audit
- build a bunch and give them to people and ask their opinions
Implications
Now one can have Athena passwords (etc.) that are just as strong as our other network passwords but still usable for interactive login.
Downloads
- schematic
- errata:
- Y1 is 16M not 8M
- C5 is 10000p not 4700p
- D1 can be any Schottky diode meeting or exceeding the properties of the B160-E3
- note:
- resistor values on page 2 are not to be substituted!
- errata:
- Gerber plot files
- STL files
- caution: needs extra 3-4mm “spacer” material
- system software